Single Sign-On allows organizations to use their already defined domain authentication and not require users to create a unique username/password for Serviceaide Intelligent Service Management.
...
To enable and configure Single Sign-On, perform the following tasks:
- Validate Prerequisites
- Export Identity Provider Certificates
- Configure SAML Single Sign-On in CSM
- Add CSM As a Trusted Service Provider in the Identity Provider
- Configure Identity Provider to Send User Identifier As Name ID
Prerequisites
Before you start the configurations, ensure that the following conditions are met:
...
If the export is successful, the certificate is saved at the location that you specified. You can open the certificate in any text editor, like Notepad.
Configure SAML Single Sign-On in Intelligent Service Management
...
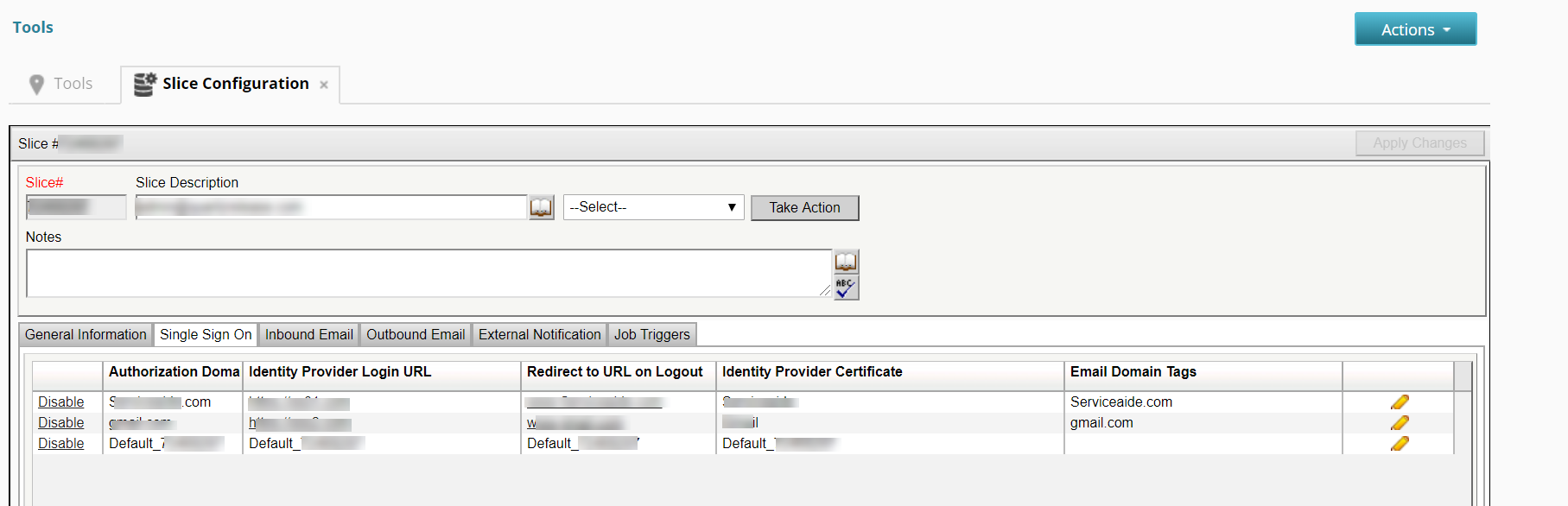
- Navigate to MANAGE> ADMINISTRATION> Tools> Slice Configuration> Single Sign On.
- To add an SSO configuration, click the + icon and perform the following actions:
- Enter the domain name, IdP login URL, and the redirect URL for logout.
- Copy the entire text from your Signing Certificate and paste it into the Identity Provider Certificate text box.
- Enter the email domain in Email Domain Tags text field. The email domain helps decide the ticket URL for outbound communications and the logout URL of the logged in user. You can add multiple email domains separated by semicolon.
Note: When multiple SSO configurations are set up, you can have only one email domain tag as empty.
- Create an entry with default Authorization domain information to support Organizations or domains that do not use SSO.
- Set Authorisation Domain to Default_<Slice number> and Email Domain Tags to specific domain or empty. This ensures that default URL (Non SSO URL) is sent in any communication sent out by the system.
Note: Only one entry for default (Non SSO) URL should be created.
Save the SSO configuration.
- To edit an SSO, click the pencil icon.
- To enable or disable an SSO, click Enable or Disable according to your choice.
After the Single Sign-On is configured in Intelligent Service Management, the metadata becomes available online. The URL to the metadata file varies for different instances of the application. Consider the following examples:
...
Add the metadata that is generated from Intelligent Service Management to your IdP to enable the SAML communication between them. For information about generating the metadata, see Configure SAML Single Sign-On in CSM.
Follow these steps on Microsoft ADFS 3.0:
- Log in to the IdP server and navigate to Administrative Tools> ADFS 3.0 Management> Relying Party Trusts> Add Relying Party Trust.
- Follow the instructions in the Add Relying Party Trust wizard to add the metadata.
- Verify that the following conditions are met:
- The Permit all users to access this relying party option is selected.
- An entry for Intelligent Service Management is displayed in the Endpoints tab.
- The Secure Hash Algorithm (SHA) value under the Advanced tab is set to SHA-1.
- On the Finish page, select Open the Edit Claim Rules dialog for this relying party trust when the wizard closes. The Edit Claim Rules dialog helps you set the attributes for identifying a user.
- Add user identification attributes in the Edit Claim Rules dialog. For more information about claim rules, see Configure Identity Provider To Send User Identifier As Name ID.
Intelligent Service Management is added as a trusted service provider in your IdP.
...
- Access the Edit Claim Rules dialog as instructed in Add CSM as Trusted Service Provider in the IdP.
- Click Issuance Transform Rules, Add Rules. Select the rule template Send LDAP Attributes as Claim and click Next.
- Configure the claim rule:
- Specify a name for the rule. For example, Send Principle as Name ID.
- Select the location for storing this rule. For example, Active Directory.
- Map the LDAP attributes to outgoing claim type. For example, LDAP Attribute - User Principle Name and Outgoing Claim Type - Name ID.
- Click Finish and confirm that the new rule is displayed in the Issuance Transform Rules tab.
- Click Apply and then click OK.
...